Consider this scenario:
A financial institution has not implemented access control. Employees at all levels, including interns and administrative staff, have unrestricted access to clients’ financial records. Without proper access control, sensitive information such as account details, transaction history, and personal data could be accessed, modified, or stolen by unauthorized individuals. This lack of security can lead to significant data breaches, resulting in financial loss, identity theft, and severe reputational damage to the institution.
In such a scenario, it is crucial to implement access control.
Introduction
Access control and permission management are crucial in protecting sensitive information from unauthorized access and misuse. They ensure that only authorized individuals can access, modify, or delete data. As a result, the core principles of the CIA triad—confidentiality, integrity, and availability-are preserved. CIA is enforced through AAA (authorization, authentication, and accounting.
This article will explore several techniques for effectively managing access control and permissions, ensuring that only necessary parties have access to sensitive data.
Access Control & Permission Management
Access control and permission management are two essential components of information security. To have proper access control and permission management, it is crucial to know more about them.
What is Access Control?
Access control is the combination of processes, policies, and technologies used to regulate who can view, use, or modify data in a computing environment. Its primary goal is to ensure that only authorized individuals or systems access specific data or resources, protecting sensitive information from unauthorized access, use, or modification.
There are three key concepts of access control. They are authorization, authentication, and accounting (AAA).
1. Authentication
This is the process of verifying the identity of a user, system, or entity.
Common Authentication Methods
- Passwords
- Biometrics
- Tokens

2. Authorization
After authentication, authorization determines what the authenticated user is allowed to do. Authorization defines the permissions associated with each authenticated user, such as which resources they can access and what actions they can perform on those resources.
3. Accounting
Accounting is the process of tracking user activities and access to resources. Logs are maintained to record who accessed what, when they accessed it, and what actions were taken. This is critical for monitoring, forensic analysis, and compliance purposes.
What is Permission Management?
Permission management is the process of defining, administering, and enforcing the permissions granted to users or systems to access, modify, or interact with resources in a computing environment.
Importance of Access Control & Permission Management
Access control and permission management are critical components of an organization’s security strategy. They protect sensitive information from unauthorized access, ensure data integrity and confidentiality, comply with regulatory requirements, and enhance operational efficiency. By implementing access control measures and effective permission management practices, organizations can mitigate risk, build trust, and maintain a secure and reliable information environment.
Strategies for Access Control
There are four types of access control.
1. DAC (Discretionary Access Control)
DAC is an access control method where the resource owner or administrator can decide who can access their resources and what permissions they have.
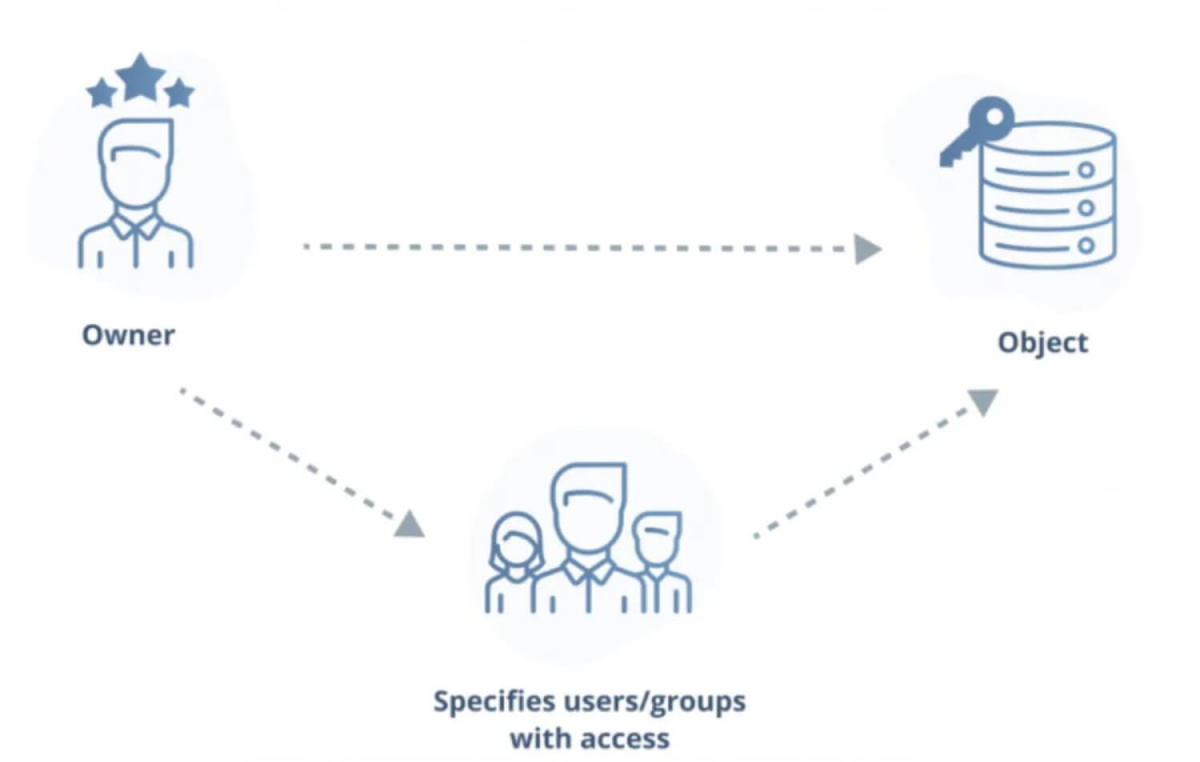
Advantages of DAC
- Flexibility: Users have the freedom to grant and revoke access as necessary.
- Ease of Use: Simple to implement and manage on a small scale.
Disadvantages of DAC
- Security Risks: Prone to accidental or intentional misuse by users who may grant access inappropriately.
- Scalability Issues: Difficult to manage in large organizations due to the decentralized nature of control.
2. MAC (Mandatory Access Control)
MAC is very different than DAC. It is a strict access control model where access rights are regulated by a central authority rather than the data owner. In the diagram below, both users and data are classified, and access is granted based on these classifications.
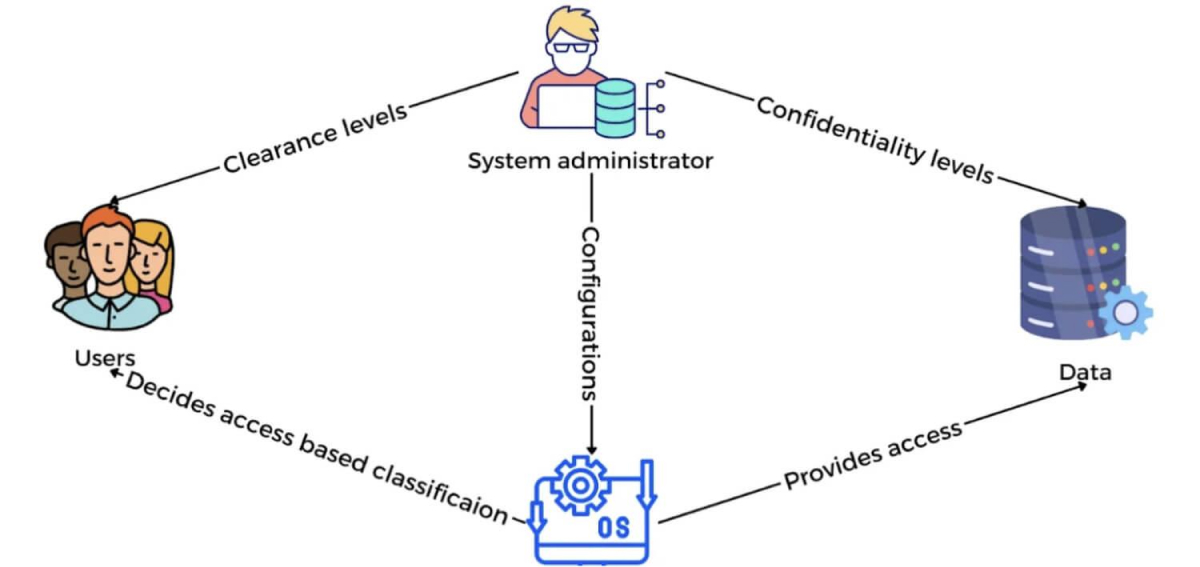
Advantages of MAC
- High Security: Ensures strict compliance with security policies, making it suitable for highly sensitive environments.
- Reduced Risk of Breaches: Minimizes the chance of unauthorized access through stringent controls.
Disadvantages of MAC
- Complexity: More complex to implement and manage due to the extra layer of security.
- Limited Flexibility: Users cannot easily change access permissions, which may slow down operational processes.
Data Peace Of Mind
PVML provides a secure foundation that allows you to push the boundaries.

3. RBAC (Role Based Access Control)
RBAC assigns access permissions based on roles within an organization. Users are assigned roles, and each role has predefined permissions, simplifying the management of user privileges.
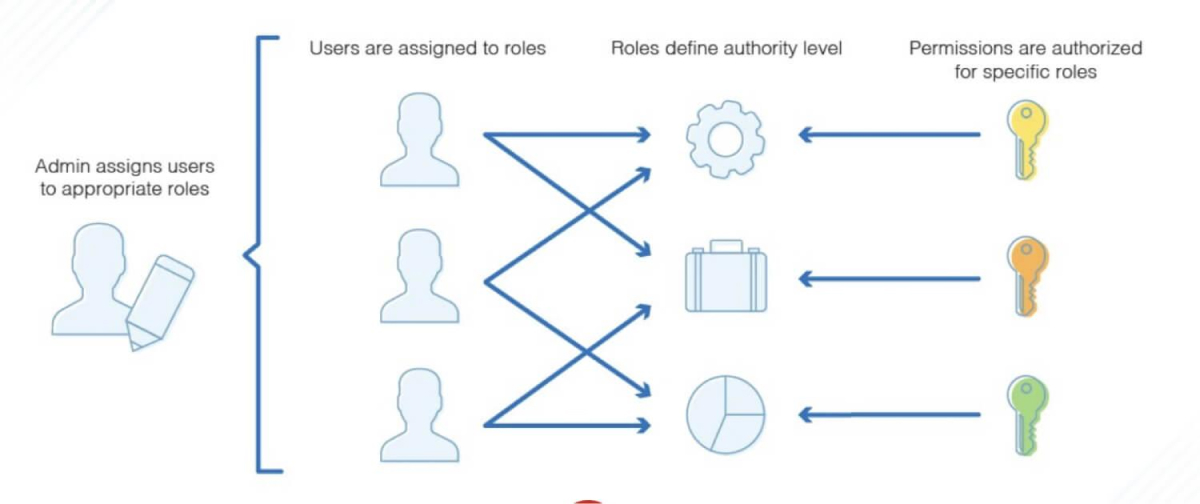
Advantages of RBAC
- Ease of Management: Simplifies the process of assigning and modifying user permissions.
- Scalability: Suitable for large organizations with many users and roles.
- Consistency: Ensures consistent application of access policies across the organization.
Disadvantages of RBAC
- Role Explosion: Over time, the number of roles can become large and difficult to manage.
- Initial Setup: It can be time-consuming to set up roles and assign appropriate permissions.
4. ABAC (Attribute Based Access Control)
ABAC grants access based on attributes (characteristics) of the user, resource, and environment. It provides a more dynamic and flexible approach compared to other models.
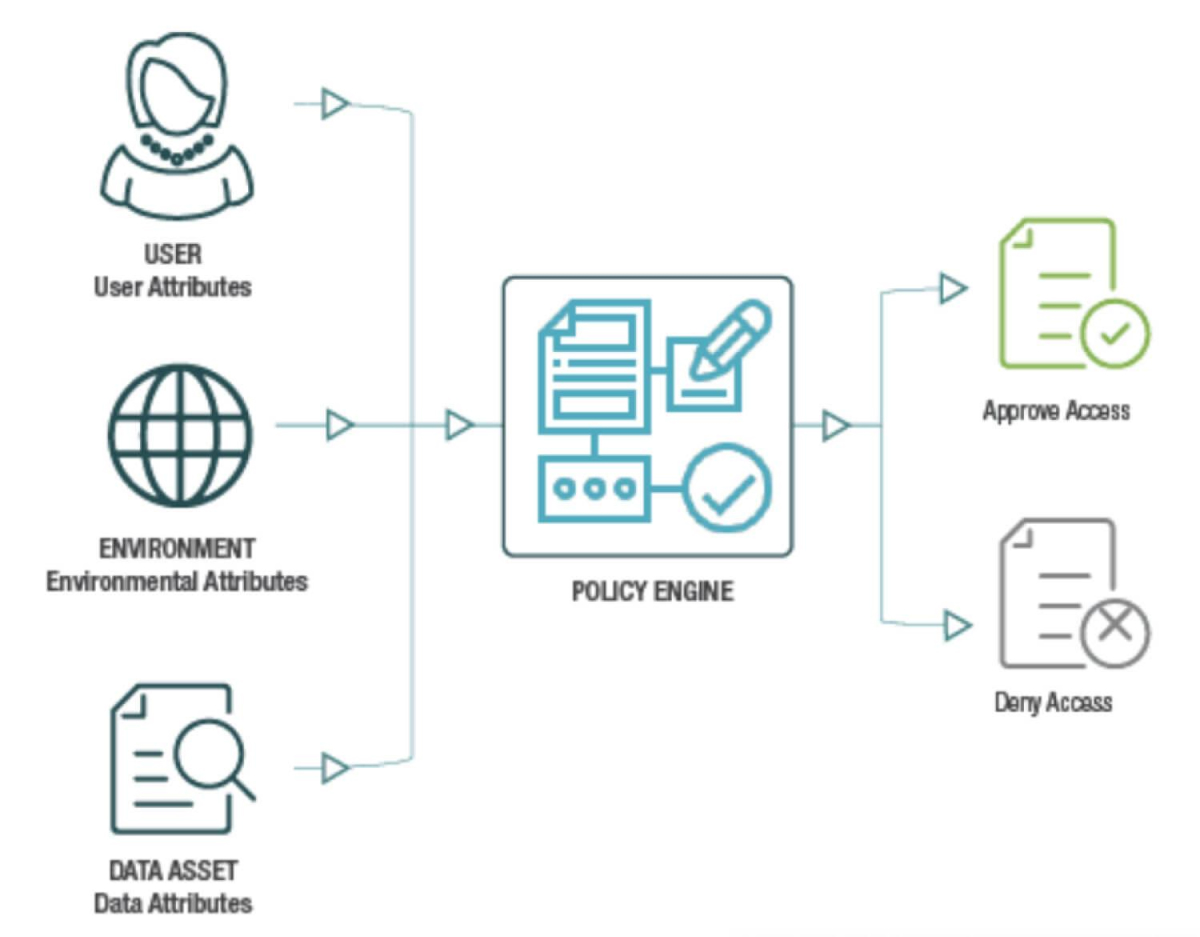
Advantages of ABAC
- Flexibility- Highly flexible and adaptable to various scenarios and changing conditions.
- Granular Control- Provides fine-grained control over access decisions based on multiple attributes.
Disadvantages of ABAC
- Complexity- More complex to implement and manage due to the need for detailed attribute definitions and policy creation.
- Performance Overhead- This can introduce performance overhead due to the real-time evaluation of attributes and policies.
Principles for Effective Access Control
Implementing effective access control involves following the fundamental principles designed to enhance security, minimize risks, and ensure the integrity of systems and data. Three key principles are the principle of least privilege, separation of duties, and need-to-know basis.
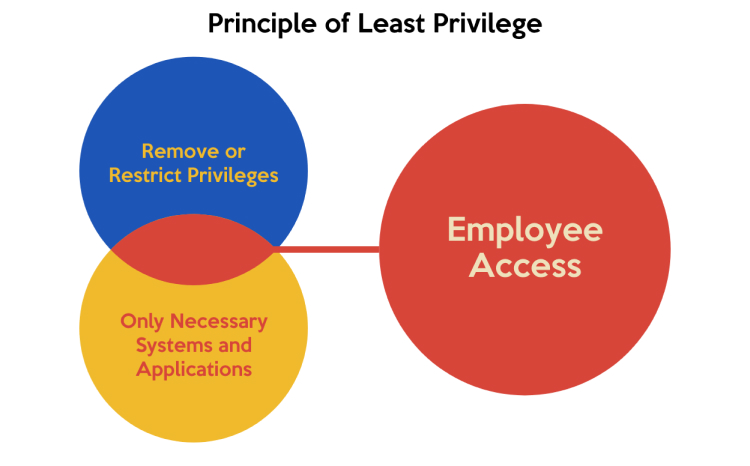
1. Principle of Least Privilege
As explained by the name itself, the principle of least privilege (PoLP) means a user or entity should only have access to the specific data, resources, and applications needed to complete a required task.
Without this principle, organizations can create over-privileged users or entities that increase the potential for breaches.
2. Separation of Duties
Separation of Duties (SoD) is the principle of not allowing one user to misuse the system by giving them enough privileges. For example, the person authorizing a paycheck should not also be the one who can prepare them.
3. Need-to-Know Basis
The need-to-know basis principle restricts access to information to only those individuals who need it to perform their specific tasks. This principle ensures that sensitive information is only accessible to those whose roles require it.
How to Implement Effective Access Control
Implementing effective access control involves a series of strategic decisions to ensure that only authorized users have access to specific resources. By following the steps below, you can effectively implement access control.
1. Define the Right Strategy of Access Control
As explained, there are four models of access control, namely DAC (discretionary access control), MAC (mandatory access control), RBAC (role-based access control), and ABAC (attribute-based access control). Choosing the appropriate access control model is crucial for aligning with your organization’s security needs, operational requirements, and regulatory obligations.
For example, larger organizations may benefit from RBAC due to its scalability, whereas smaller organizations might find DAC more manageable.
2. Define the Right Principle to Use
Choosing the appropriate principle is also as crucial as selecting the right strategy for access control. As explained, there are three principles: the principle of least privilege (PoLP), separation of duties (SoD), and need-to-know basis.
3. Define Right Permissive Policies
Creating and enforcing appropriate access policies is key to maintaining security and operational efficiency. When creating permissive policies, it should clearly define what resources require protection and what constitutes authorized access. Furthermore, permission policies should be reviewed and updated regularly.
4. Strong User Authentication and Authorization Approaches
Strong authentication and authorization mechanisms are vital for ensuring that access control policies are effectively enforced.
Strong authentication mechanisms include multi-factor authentication (MFA), biometric authentication, or strong password policies.
Authorization can be handled using different models of access control, such as RBAC and ABAC.
Best Practices for Access Control
Implementing effective access control requires a combination of strategic auditing, automated tools, and ongoing training. By following the practices below, proper access control can be implemented.
1. Regular Audits
It is essential to regularly audit access permissions to ensure alignment with job roles. Unused permissions should be removed to minimize security risks. It is important to maintain detailed logs of access activities for compliance and review.
2. Automated Tools
Automated tools such as Identity Access Management (IAM) systems can be used to manage user access centrally. Furthermore, IAM can be used for automated user provisioning and role management. It is important to use automated tools to enforce access policies consistently.
3. Trainings
After implementing access control policies, there should be regular sessions to educate employees on the policies and best practices. The training should be different based on user roles. Furthermore, it is important to run ongoing programs to promote a security-first mindset.
Wrapping Up
Implementing effective access control and permission management is vital for protecting sensitive environments. By selecting the right access control model, adhering to key security principles like the principle of least privilege, separation of duties, and the need-to-know basis, and establishing clear, enforceable policies, organizations can significantly reduce the risk of unauthorized access and data breaches.
An appropriate access control model can further ensure that access rights are appropriately managed and enforced. Continuous monitoring, regular audits, and user education are essential for maintaining the integrity and effectiveness of access control measures. Together, these strategies create a strong framework that protects sensitive data, ensures compliance, and supports the secure operation of the organization.
Thank you for reading.