
Data In Organizations
Data is an essential asset to any business. By leveraging data, companies can make critical decisions that help define their success. Therefore, data is an important yet sensitive asset to any organization.
So, it must be protected to ensure that confidentiality, integrity, and availability are kept (CIA). To do so, you need to do two things:
- Restrict access to data assets that reside across multiple clouds and environments
- Verify the authenticity of the individuals trying to access that data.
That’s where Data Access Control comes in.
What is Data Access Control?
Data access control is a security mechanism that you can adopt to restrict access to data by defining a set of policies.
Doing so lets you continuously determine who has access to what data at any given time.
This ensures that the personally identifiable information (PII), intellectual property, and other sensitive information you collect remains safe.
To do so, you must understand two components that drive data access control.
- Authentication: This process verifies the identity of a user, system, or application attempting to access data. It involves confirming the validity of provided credentials, which can include usernames and passwords, biometrics, security tokens, or other authentication factors. The goal is to ensure that the entity attempting access is legitimate and has the right to access the requested data.
- Authorization: Once a user’s identity is authenticated, the authorization process comes into play. Authorization determines the specific permissions and actions that the authenticated user is allowed to perform within the system. This involves defining and assigning role and access levels based on the user’s identity and responsibilities.
To effectively implement data access control, you must ensure that both components are properly implemented.
If not, you’d have users belonging to a system able to perform all CRUD operations (Create, Read, Update, and Delete).
So, data access control focuses on leveraging the principle of least privilege, managing access rights based on a role in the organization, and defining and limiting what data they have access to.
Data Peace Of Mind
PVML provides a secure foundation that allows you to push the boundaries.

What are the types of Data Access Control?
You can apply data access control using four techniques.
Discretionary Access Control (DAC)
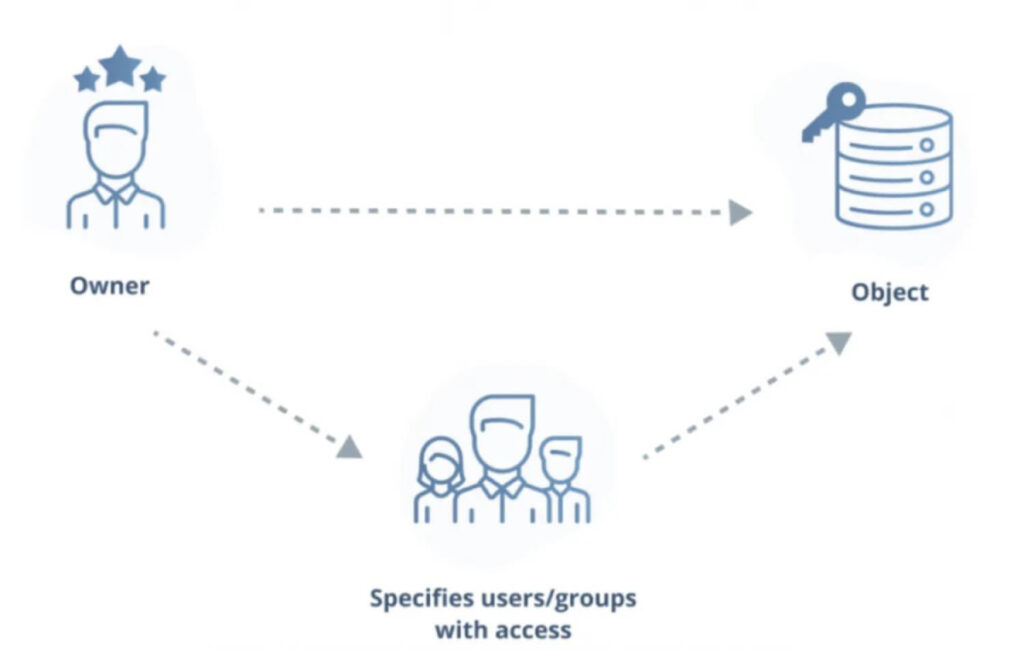
DAC relies on the owner or administrator of the resource to decide who has access permission. Simply put, the data owner decides who can access their data.
Looking at the diagram, it’s important to note that the DAC model doesn’t involve a central body governing the permissions to the object. Therefore, it follows a more decentralized permission model, making it harder for organizations to monitor who’s accessing the data.
But, this decentralized permission model makes DAC a good fit for sharing non-sensitive files within your organization.
Mandatory Access Control (MAC)
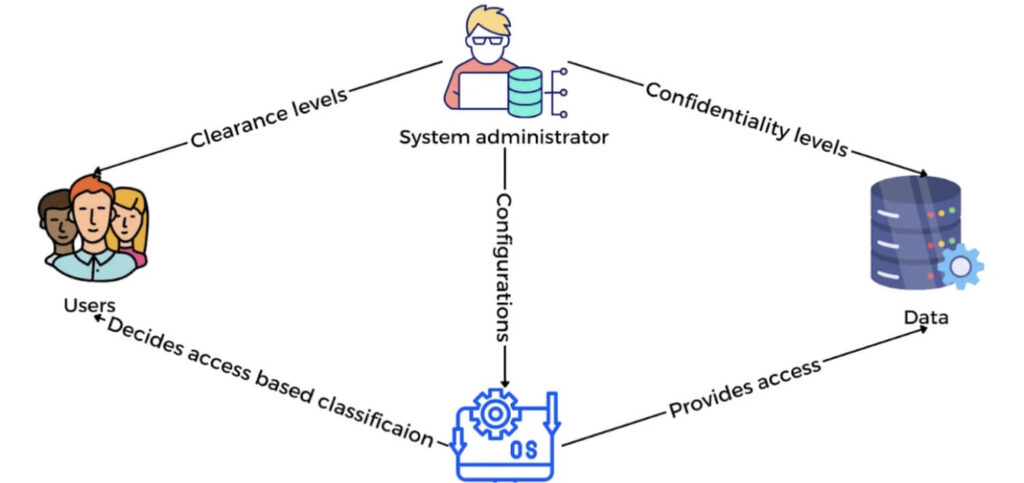
Mandatory Access Control operates on a principle different from DAC. In MAC, access permissions are not determined by the data owner but by the system administrator. This means that access decisions are based on predefined rules and security labels associated with users and data objects.
For example, MAC is heavily used in government agencies such as the military.
The military has different levels of classified information – unclassified to top secret. Likewise, different personnel within the organization require access to this information based on their roles and security clearances.
So, what happens here is –
- Each document/data gets assigned with these labels – Classified, Unclassified, Top Secret.
- Every user in the system is given a mandatory label that indicates the highest level of data they can access.
Next, when the user accesses a document, their security clearance is cross checked to see if they can access the document with the attached label.
While this offers a more centralized approach to permission management, it’s more harder to manage.
Role Based Access Control (RBAC)
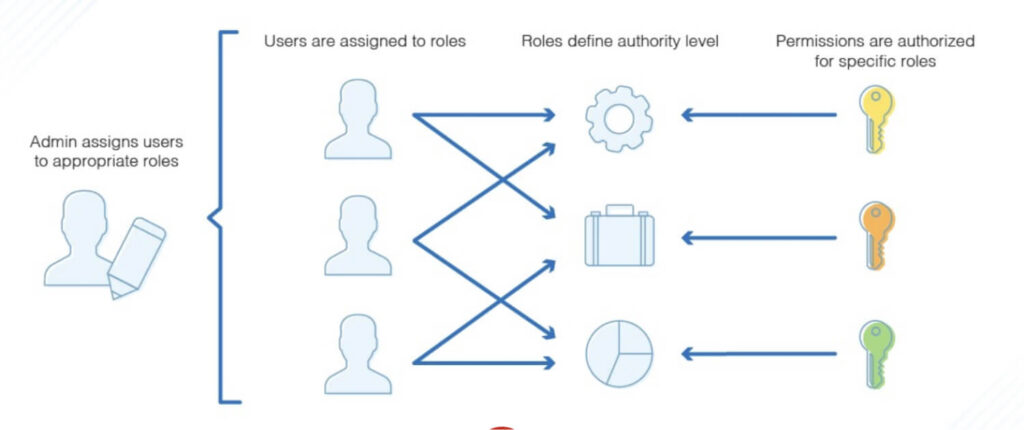
RBAC is a prevalent form of Data Access Control that most SaaS applications adopt as it aligns with the role and needs of every individual in the organization.
It uses the principle of least privilege (POLP) to assign privileges based on the needs of an individual’s role in the organization. Any user attempting to access data outside their scope is restricted.
For example, consider an application. You might have an Administrator and a Guest role. Each role has a set of permissions attached to it. For instance:
- Administrator: Can perform all CRUD operations in the system
- Guest: Can only read data in the system.
So, once you assign users to these roles, their actions will be determined by the actions permitted in the role.
By doing so, you can centrally manage permission to a group of users by managing a single role.
Attribute Based Access Control (ABAC)
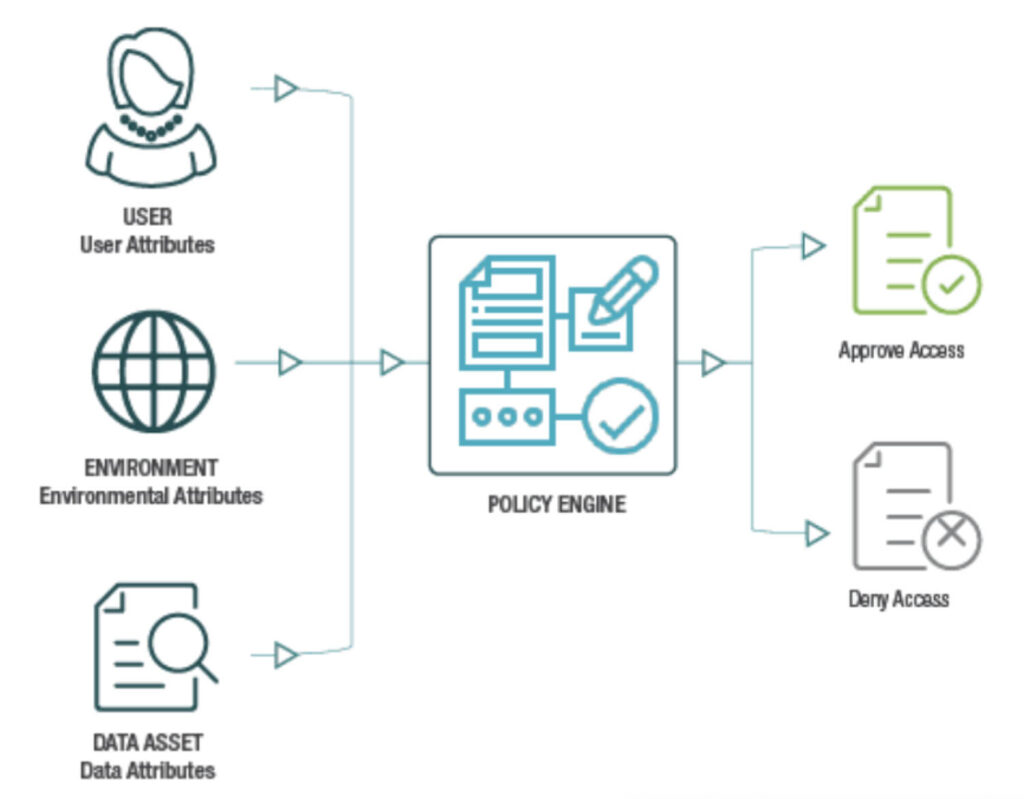
Attribute-Based Access Control (ABAC) is a flexible access control model that evaluates various attributes associated with users, data objects, and the environment to make access control decisions. Such attributes could include:
- User roles.
- Permissions.
- Environmental conditions such as location and time.
ABAC allows for dynamic and context-aware access control, enabling organizations to enforce fine-grained access policies based on specific attributes.
How To Implement Data Access Control?
If you’re looking to implement a data access control system in your organization, one of the best places to get started with is by setting up an Identity and Access Management.
The AWS IAM service is one such service that lets you start building with RBAC with no effort. All you have to do is create your roles, assign permissions to the role and define the entities that can assume your role.
Using an IAM is beneficial as it:
- Offers centralized control over data across your organization
- Automates tasks such as provisioning of users, roles, groups
- Maintains compliance with regulations such as GDPR, HIPAA, PCI, and CCPA
Wrapping Up
Though the concepts for Data Access Control seem easy, they’re difficult to implement. But, if you start early, you’re able to ensure that your app and sensitive data are as secure as ever.
So, don’t treat security as an afterthought. Integrate it into your workflow.
As a best practice, consider adopting a solution that streamlines data access control processes while enhancing security through an additional layer that monitors for malicious or inappropriate access. While defining access controls is crucial, it’s equally important to implement continuous monitoring practices. Regularly check for signs of excessive permissions, unused access, and users who are no longer part of the system, ensuring that access is regularly adjusted or revoked.
This ongoing vigilance is essential for maintaining a secure data access strategy.