Organizations need to admit that no matter what industry they operate in, there will always be sensitive data being processed within the organization’s processes and functions.
Modern-day organizations depend significantly more on data than they did a decade ago. This is primarily because decisions based on data and analytics yield much higher returns since they allow organizations to take more daring risks that pay off in the long run.
With the cost of data breaches at an all-time high, organizations must prepare for the worst. This is reflected in a paradigm shift in the realm of cybersecurity.
It is no longer a matter of “IF” an organization is breached; it’s a matter of “WHEN” it will be breached.
Understanding Sensitive Data
To manage sensitive data, organizations must first understand what sensitive data is so that they are equipped to properly manage it.
What is Sensitive Data?
It is any type of data that has a significant value to an individual or organization. In each case, access to this data must be restricted to authorized personnel.
Sensitive data extends to more than data that can identify an individual; it may also include data that is related to business operations or information that could provide a competitive advantage to an organization.
Some examples of sensitive data may include:
- Personally identifiable information (PII)
- Financial information
- Health information
- Intellectual property
- Confidential communications
Importance of Effective Sensitive Data Management
Effective management of sensitive data can save an organization millions, if not billions, of dollars in fines. This is because data breaches and violations of regulations are taken seriously in most parts of the world with the introduction of data protection acts and regulations.
Nevertheless, a single data leak can expose sensitive information that can cripple business processes or any competitive advantage that the organization has over its competition.
Challenges in Sensitive Data Management
Sensitive data management may sound simple enough, but when the scale of an enterprise comes into the picture, even the simplest functions become tedious.
This is because of the complexity of the ecosystem as well as the various integrations these systems have to accommodate to share data across systems.
Looking at a modern-day enterprise, we see a lot of technological advancements and evolution in terms of the technology that is being used. This is due to the constant need for efficient and state-of-the-art tools and technologies to bridge the gap with their competitors and to improve processes.
One aspect that often gets overlooked is the balance between usability and security. It is useless to have state-of-the-art security solutions if the data cannot be accessed efficiently by its intended users. Therefore, implementing sensitive data management is often a balancing act to ensure that adequate security measures are implemented.
Data Peace Of Mind
PVML provides a secure foundation that allows you to push the boundaries.

Strategies for Effective Sensitive Data Management
There are some key strategies that organizations employ to ensure effective sensitive data management.
The following strategies focus on key areas that are common to most organizations:
1. Data Classification
Data classification is one of the most rudimental approaches to ensuring effective sensitive data management. This can be done either manually, where the user adds the classification label to the document by hand, or automatically, where a solution can classify documents by labeling them in near real-time, ensuring that no document is left unclassified.
The importance of data classification is that it allows users and other systems to identify sensitive data and what type of data is stored within a document, thus enabling users to effectively select the type of controls that need to be enforced on the specific document.
2. Access Control
Access to sensitive data must always be provided on a need-to-know basis, where users and other entities are provided access based on the job that they are required to accomplish.
Restricting access to data is an effective method of keeping sensitive data from falling into the wrong hands.
Access control may also look into the level of access that a single entity is given. This could mean that the user will only have read access to a specific piece of data but not edit access. This ensures that only authorized personnel can make changes to sensitive data.
3. Data Lifecycle Management
It is not enough to safeguard sensitive information when it is being used; effective sensitive data management involves protecting sensitive data throughout its lifecycle, from collection to disposal.
Data classification can help systems identify types of data that require special attention in terms of retention and management, while allowing the entire data lifecycle process to be automated.
However, it is always important to remember that sensitive data should only be kept if it is current and relevant to the business processes. Once data becomes outdated or irrelevant, the specific data must be disposed of appropriately so there is no chance of leakage. The specifics must be documented in a policy or procedure that looks into the data lifecycle management.
4. Monitoring and Auditing
It is not enough to manage sensitive data securely if the organization isn’t constantly monitoring and auditing its access and usage. Regularly auditing sensitive data usage will give an organization an overview of the data use and visibility of any access violations.
However, since auditing happens on a periodic basis, it is not adequate for detecting real-time threats to sensitive data. This is where monitoring comes in: to provide real-time visibility of sensitive data access and to ensure that threats are detected before they escalate into major incidents.
Implementing Sensitive Data Management Frameworks
Encompassing the best-of-breed sensitive data management is crucial for running a large-scale organization smoothly. This is where implementing sensitive data management frameworks such as GDPR or ISO 27701 ensures that industry best practices are followed across every function within the organization.
However, sensitive data management can always benefit from the implementation of cybersecurity frameworks that go along with data protection frameworks. NIST CSF and ISO 27001 are some cybersecurity frameworks that can boost the security posture of an organization so that it has more robust policies and processes to deal with sensitive data management.
Emerging Trends and Technologies in Sensitive Data Management
The world of artificial intelligence and machine learning has grown over the past couple of years, with many new introductions to detecting threats. These methods can easily be extended to sensitive data management.
Tools such as AWS Macie and Amazon GuardDuty use machine learning to discover sensitive information that is stored within your cloud infrastructure and to detect threats by correlating various types of logs. These solutions lay the groundwork for protecting your sensitive data workloads on the cloud.
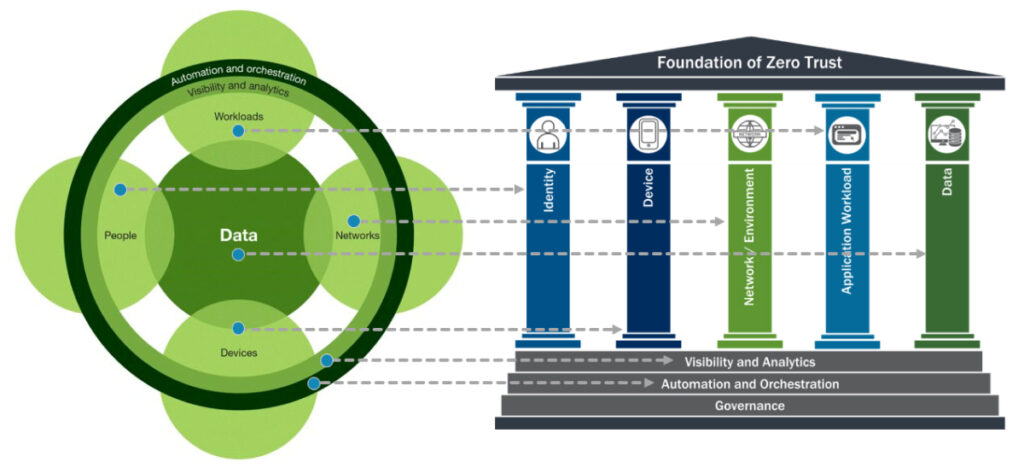
Additionally, zero trust has introduced a new way for organizations to look at how they provision access and trust internal or external resources while accessing their data. Zero trust ensures that organizations verify every request that entities make when accessing applications and data.
These types of architectures do not leave room for organizations to implicitly trust internal resources where insider threats have always been overlooked.
“Never Trust. Always Verify” is the basis of zero-trust architectures, and they play a vital role in ensuring that unauthorized actors do not get permission to access sensitive data.
Key Takeaways
Building sensitive data management processes within an enterprise is not an easy task by any means due to the sheer scale and complexity of the technology ecosystem. Therefore the strategies and frameworks discussed help organizations start applying sensitive data management from the very first stages of the data life cycle.
There are various tools that can help implement the technical controls that are required by these strategies and frameworks. However, it is important to understand that there is no silver bullet for all business requirements that may be within every organization. Therefore, customizing and choosing the specific strategies that fit the organization and business requirements will make the difference between successful sensitive data management and a catastrophic data breach!