Access control plays a major role in protecting sensitive data and ensuring privacy against cyber attacks. Access control decides who can view or use different parts of a system and what actions they can perform.
There are two main types of access control: role-based access control (RBAC) and permission-based access control (PBAC). RBAC gives permissions to roles, which are then assigned to users. PBAC, on the other hand, gives permissions directly to users or entities. This blog will discuss permission-based access control (PBAC), explaining how it works and why it’s important for modern security.
What is Permission-Based Access Control (PBAC)?
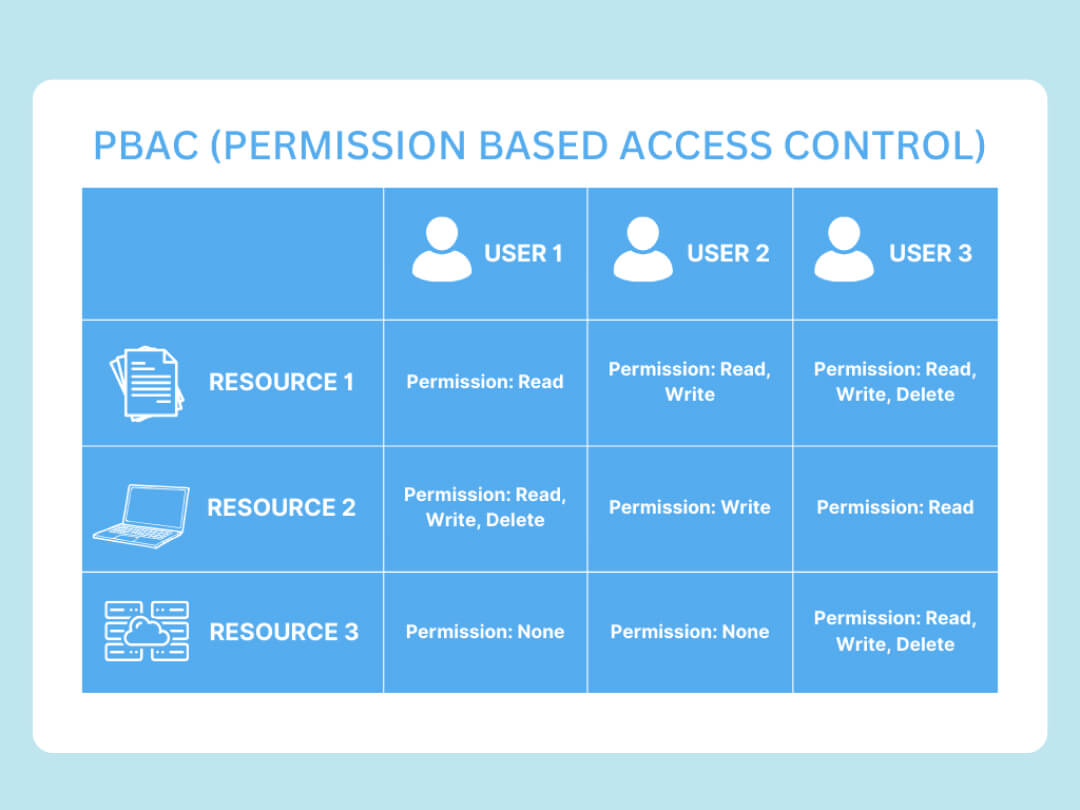
Permission-based access control (PBAC) is an access control mechanism where access rights are granted to users based on specific permissions. These permissions define various actions a user can perform on a resource, like read, write, execute, or delete. PBAC ensures that users can only perform actions they are explicitly allowed to, improving the security posture and integrity of data and systems.
Components of Permission-Based Access Control
PBAC has several key components:
- Permissions: Specific rights granted to users, defining what actions they can perform on resources. For example, a user might have permission to read a file or write to a database.
- Users: Individuals or entities that require access to resources.
- Resources: Objects or data that need protection, like files, databases, or applications.
- Access Control Lists (ACLs): Lists that specify which users or roles have which permissions on a resource.
How Permission-Based Access Control Works
In PBAC, each user is assigned specific permissions to determine what they can do with different resources. These permissions are stored in an Access Control List (ACL) for each resource. When a user attempts to access a resource, the system checks the ACL and decides if the user has the necessary permissions. If the required permissions are present, access is granted; otherwise, access is denied.
For example, consider a file system where different files require different permission levels:
- Public Documents: Accessible to everyone.
- Departmental Reports: Accessible to certain users for updates.
- Financial Records: Restricted to finance personnel.
Permissions:
- Alice (project manager) has read access to public documents, write access to departmental reports, and no access to financial records.
- Bob (accountant) has read access to public documents, write access to departmental reports, and read and write access to financial records.
How It Works:
- Alice accesses a public document. The system checks the ACL, finds that Alice has read permission, and grants her access.
- Alice tries to access a financial record. The system checks the ACL, finds that Alice has no permission, and denies her access.
Implementing PBAC Using AWS IAM
Now, let’s see how we can implement the above scenario with AWS IAM. Here, I will be using AWS CLI commands.
Step 1: Create IAM Users
aws iam create-user --user-name Alice aws iam create-user --user-name Bob
Step 2: Create IAM Policies
Create a JSON file named public-documents-policy.json with the following content:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"s3:GetObject",
"s3:ListBucket"
],
"Resource": [
"arn:aws:s3:::public-documents-bucket",
"arn:aws:s3:::public-documents-bucket/*"
]
}
]
}
Then, create the policy using the AWS CLI command below.
aws iam create-policy --policy-name PublicDocumentsPolicy --policy-document file://public-documents-policy.json
Use the same process to create policies for departmental reports and financial records.
Data Peace Of Mind
PVML provides a secure foundation that allows you to push the boundaries.

Step 3: Attach Policies to Users
// Attach Policies to Alice:
aws iam attach-user-policy --user-name Alice --policy-arn arn:aws:iam::<AWS_ACCOUNT_ID>:policy/PublicDocumentsPolicy aws iam attach-user-policy --user-name Alice --policy-arn arn:aws:iam::<AWS_ACCOUNT_ID>:policy/DepartmentalReportsPolicy
// Attach Policies to Bob:
aws iam attach-user-policy --user-name Bob --policy-arn arn:aws:iam::<AWS_ACCOUNT_ID>:policy/PublicDocumentsPolicy aws iam attach-user-policy --user-name Bob --policy-arn arn:aws:iam::<AWS_ACCOUNT_ID>:policy/DepartmentalReportsPolicy aws iam attach-user-policy --user-name Bob --policy-arn arn:aws:iam::<AWS_ACCOUNT_ID>:policy/FinancialRecordsPolicy
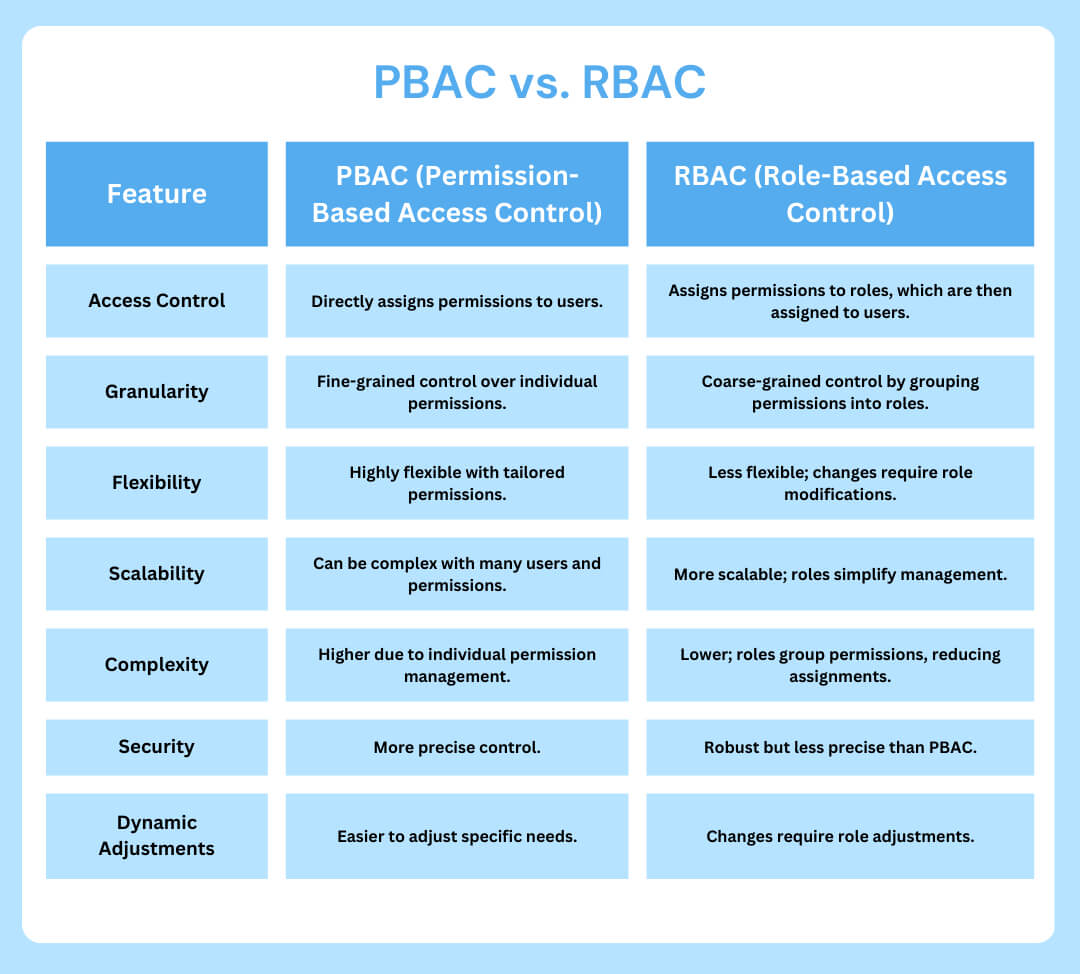
PBAC vs. RBAC
Role-based access control is another popular method to manage access to resources in software systems. Although PBAC and RBAC serve similar purposes, there are also some major differences. The table below will give you a clear understanding of the similarities and differences between PBAC and RBAC:
Benefits of Permission-Based Access Control
- Granular Control: PBAC allows you fine-grained control over who can access specific resources and what actions they can perform.
{
"resource": "employee_records",
"permissions": {
"HR": ["read", "write"],
"Finance": ["read"]
}
}
- Improved Security: Reduces the risk of unauthorized access and potential data breaches, enhancing the organization’s overall security posture.
- Compliance: Helps organizations comply with regulatory requirements like GDPR and HIPAA by controlling access to sensitive data.
{
"resource": "patient_records",
"permissions": {
"Doctor": ["read", "write"],
"Nurse": ["read"],
"Admin": ["read", "write"]
}
}
- Flexibility: PBAC can be designed to meet an organization’s specific needs. It allows you to address context-sensitive scenarios and changing organizational needs.
Drawbacks of Permission-Based Access Control
- Complexity: Managing permissions for many users and resources can become complex and time-consuming, leading to errors and inconsistencies in access control policies.
- Maintenance: It requires significant effort to update ACLs as roles and responsibilities change over time.
- Potential for Over-Restriction: PBAC can lead to overly restrictive access controls, reducing the organization’s productivity since users may not have the necessary permissions to perform their tasks efficiently.
Use Cases of PBAC
PBAC is widely used for environments where fine-grained, specific access control is needed. Some common use cases include:
- Small to Medium Enterprises (SMEs): Used in document management systems where each document’s access is tightly controlled based on user-specific permissions.
- Research Projects: In research labs, individual researchers have specific permissions to access certain datasets or experiments. Each researcher’s access is customized based on their involvement in different projects.
- Custom Software Applications: Manages user-specific access in custom-built systems, such as a CRM, where users will have specific access rights.
- File Sharing Services: Customizing access to different folders and documents based on each user’s tasks and needs rather than grouping them into predefined roles.
Conclusion
Permission-based access control is a security mechanism that helps organizations protect their resources by granting access based on specific permissions. With PBAC, organizations can achieve granular access control to protect sensitive data, simplify operations, and ensure that only authorized users can access important information.