What is Homomorphic Encryption?
Homomorphic encryption is the conversion of data into ciphertext that can be analyzed and worked with as if it were still in its original form.
It enables complex mathematical operations to be performed on encrypted data without compromising the encryption.
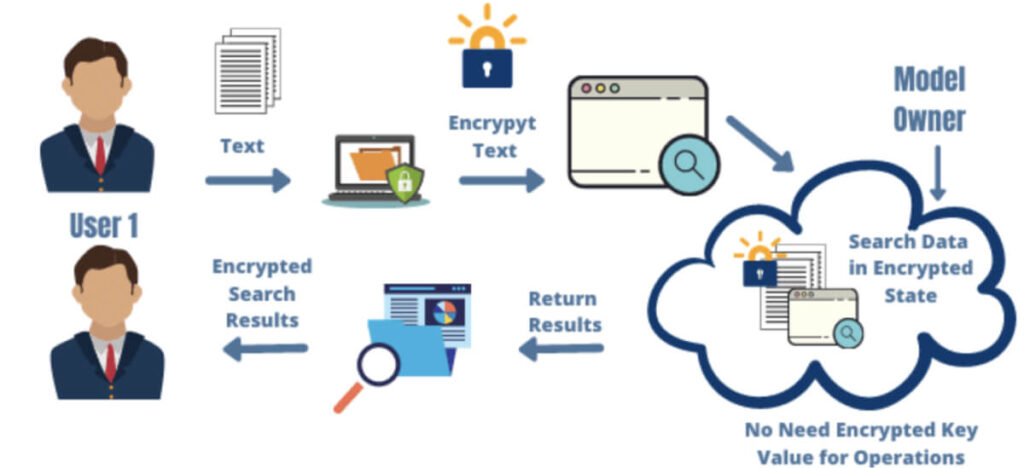
For instance, consider the following scenario:
A medical research institution wants to analyze patient data from several hospitals to study the effects of a new medication. Due to privacy regulations like HIPAA, they are not allowed to directly access and analyze the data. So, each hospital encrypts its patient data using homomorphic encryption before sending it to the research institution.
This is what the initial data set might look like:
Ages of patients: [25, 30, 45, 50]
Upon encryption, this is what an expected output would look like:
Age of patients: [Enc(25), Enc(30), Enc(45), Enc(50)]
The encrypted data is not directly understandable, but analysis can be carried out on the dataset. So, the research center can perform calculations on the encrypted data to get the average age, which would also be encrypted.
Finally, the authorized party would decrypt the calculated response and get the average age without ever seeing the individual age entries!
This is the power of homomorphic encryption. It lets you analyze data without even seeing it, thus remaining compliant by preserving the privacy of the data.
Types of Homomorphic Encryption
There are several different types of homomorphic encryption.
1. Partially Homomorphic Encryption (PHE)
This type of encryption only supports very limited analytical methods for encrypted data. In fact, it only supports either addition or multiplication on ciphertexts, but not both.
Because of its simplicity, these encryption schemes are relatively easy to design. But they can’t be used everywhere.
PHE is widely used in applications where only one type of operation (addition or multiplication) is needed, such as encrypted voting systems where votes are tallied (added) without revealing individual votes.
2. Somewhat Homomorphic Encryption (SHE)
This type of encryption supports a limited number of both addition and multiplication operations on ciphertexts.
The limit is due to noise that accumulates with each operation, which can eventually render the decryption incorrect if too many operations are performed.
Due to its complexity, it’s more difficult to design.
SHEhis is widely used in applications requiring a mix of operations on encrypted data, such as certain types of encrypted data analysis, with the limitation that only a small number of operations can be performed.
3. Fully Homomorphic Encryption (FHE)
This type of encryption supports an unlimited number of both addition and multiplication operations on ciphertexts. It overcomes the limitations of PHE and SHE by incorporating techniques to manage and mitigate noise accumulation.
FHE can be used in any scenario. Due to its ability to support complex computations on encrypted data, it can be used in cloud computing, secure data analysis, and privacy-preserving machine learning.
A common use case allows users to leverage cloud services for computation without exposing their sensitive data.
Data Peace Of Mind
PVML provides a secure foundation that allows you to push the boundaries.

4. Leveled Homomorphic Encryption (LHE)
This is a variant of FHE designed to handle a predetermined depth of operations.
Though FHE can theoretically handle an unlimited number of operations, doing so may be impractical due to computational demands. Therefore, LHE optimizes performance by limiting the number of operations.
LHE offers a balance between the flexibility of FHE and the efficiency of SHE, making it suitable for certain types of data analysis and cloud computing tasks, and it is useful for applications where the complexity of the required operations is known in advance.
Use Cases of Homomorphic Encryption
Homomorphic encryption is extremely useful in scenarios where data needs to be shared with third-party services for analysis.
For instance, companies like Meta leverage these encryption algorithms to share data with third-party agencies so that they can perform analytics on user data without being able to view the original data, thus providing more private targeted advertising.
Additionally, homomorphic encryption is useful in scenarios where regulatory compliance is essential. For example, it can help companies outside of the European Union (EU) adhere to General Data Protection Regulation (GDPR) requirements-the GDPR requires EU data to remain in the EU or countries with equivalent data security standards, but these rules don’t apply to encrypted data.
Challenges of Homomorphic Encryption
However, implementing homomorphic encryption is not entirely beneficial. Preserving data privacy in this way comes at a cost:
1. Performance and Efficiency
- Computational Overhead: These operations are significantly slower than operations on plaintext due to the complex mathematical processes involved in maintaining the encrypted state during computations.
- Resource Intensiveness: These require more memory and processing power compared to traditional encryption methods. Therefore, this can be a limiting factor in resource-constrained environments or for applications requiring real-time processing.
2. Data Size and Bandwidth
- Increased Data Size: Encrypted data under HE schemes tends to be much larger than the original plaintext. This increase in data size can pose challenges for storage and transmission, especially in bandwidth-limited scenarios.
- Bandwidth Requirements: Transmitting HE-encrypted data across networks requires more bandwidth than unencrypted or traditionally encrypted data, potentially leading to increased costs and reduced efficiency.
3. Scalability
The performance and efficiency challenges of HE make it difficult to scale applications to handle large datasets or high volumes of transactions, especially for applications requiring near-real-time processing.
Wrapping Up
Homomorphic encryption is something everyone should be aware of. Its adoption could help organizations remain compliant with data protection acts across the globe and contribute to keeping PII data private and ensuring its ethical use.