What is Permission Management?
Permissions are key in ensuring security within your organization.
It helps define:
- Who has access to data?
- What data can be accessed?
- How long is the access valid?
Managing permissions effectively allows organizations to ensure that only authorized individuals can access the necessary data.
More specifically, permission management helps you:
- Protect Sensitive Data: By carefully defining who has access to what data, organizations can prevent unauthorized access and potential data breaches. This is especially critical for industries handling personal information (PII), financial records, or proprietary business data.
- Minimize Data Breaches: Only trusted and verified sources can access sensitive data, reducing the risk of data breaches.
- Meet Legal Requirements: Sometimes, organizations adopt strict permission management to comply with a governing body, such as GDPR or ISO, to gain more credibility or avoid fines.
Now that you know why permissions are needed let’s see how they are managed.
Core Concepts of Permission Management
At its core, every permission management model has three aspects:
- User: A user is an entity that interacts with the system.
- Role: Each entity interacting with the system is associated with a single role.
- Policies: Each role has a set of policies defining the user and the actions each role can execute (reads/writes/deletes/updates).
For example, consider the following figure:
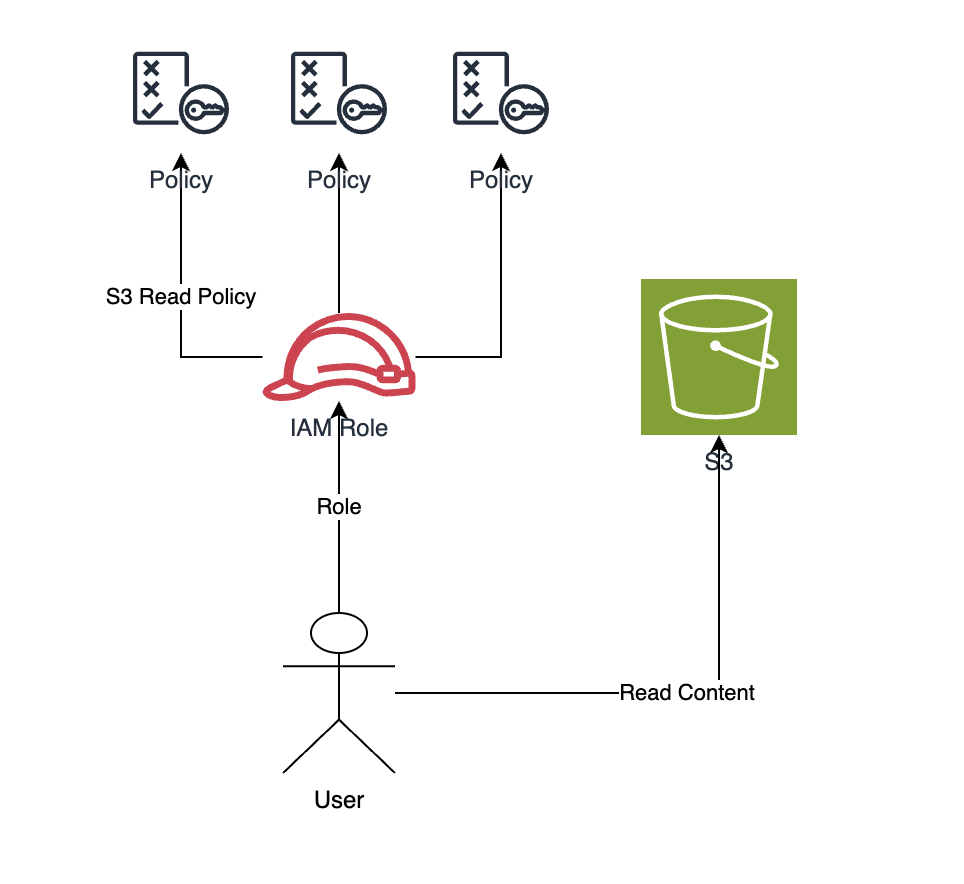
The figure above depicts a user trying to read contents from an S3 bucket. This request will be successful as this user is assuming a role that has a policy that allows S3 Reads.
Simply put, the order of execution would be as follows:
- A role is created, and policies are attached.
- A user assumes the role.
- The user requests a resource.
- During the request, verify that the role permits access to the resource.
- If so, provide access; otherwise, show a forbidden response.
Models of Permission Management
Effective permission management requires a clear understanding of the different types of permission models available. Here are some of the most popular models used today:
1. Role-Based Access Control
Role-based access control (RBAC) is one of the most commonly used models in permission management. In this approach, permissions are not assigned directly to users (similar to our S3 example earlier). Instead, users are assigned to roles, and roles are given specific permissions.
This significantly simplifies permissions management by grouping them into roles that reflect various functions.
2. Attribute-Based Access Control
Attribute-based access control (ABAC) is a more dynamic and flexible model than RBAC.
In ABAC, access rights are granted to users based on attributes, which can include:
- User attributes (e.g., department, job title).
- Resource attributes (e.g., data sensitivity, resource owner).
- Environmental attributes (e.g., time of day, location).
Data Peace Of Mind
PVML provides a secure foundation that allows you to push the boundaries.

3. Discretionary Access Control
Discretionary access control (DAC) is a model in which the owner of a resource decides who can access that resource and what kind of access they have.
In DAC, access rights are typically assigned directly to individual users or groups.
For example, you might give access to a particular user in your organization to manage the AWS infrastructure through an Identity Access Management (IAM) user role.
4. Mandatory Access Control
Mandatory access control (MAC) is a more rigid and structured model than DAC.
In MAC, access decisions are made based on predefined policies set by a central authority, which users cannot change. Access rights are typically based on information classification and user security clearance.
For example, consider a government organization in which documents are classified into different levels, such as Confidential, Secret, and Top Secret. The central authority defines and enforces these rules, and individual users cannot alter them, ensuring strict control over sensitive information.
Implementation Strategies
Now that we understand the types of access control, let’s see how we can implement them in real life.
Start with an IAM
Start with an IAM tool such as AWS IAM or an Azure Active Directory. You can use an IAM tool to:
1. Create IAM Users: Users can be assigned specific permissions based on their roles and responsibilities.
aws iam create-user --user-name new_user
2. Define IAM Roles: Roles can be defined based on job functions, such as “Administrator,” “Developer,” or “Read-Only User.”
aws iam create-role --role-name DeveloperRole --assume-role-policy-document file://trust-policy.json
3. Define IAM Policies: Policies can be fine-grained, defining specific actions like “read,” “write,” and “delete,” or more coarse-grained for broader permissions.
These will allow your team to define what actions can be taken and who can do them.
Define your IAM Policies
After you’ve created your IAM Users in your Active Directory, you can start to define your policies. It’s important to define and document your access policies. This includes specifying who needs access to what resources and under what conditions.
Policies should be detailed and aligned with your organization’s security requirements.
Ensure that your policies conform to the following best practices:
- Least Privilege: Users should have the minimum level of access required to perform their tasks. For example, if someone wants access to a database table, they should only have access to that table, not the entire database.
- Separation of Duties: To prevent fraud and errors, no single user should have control over all aspects of any critical process.
- Access Reviews: Regularly review and update access policies to reflect organizational changes.
Bring in External Tools
Next, you can bring in your external integration tools, such as SAML or OAuth. This will help you centrally manage your users and permissions so that you can clearly define what tools they have access to and revoke them in a central location.
Wrapping Up
By following these steps, you’re guaranteed to improve the security posture within your organization and seamlessly ensure that everyone has the right permissions at the right time.