Dynamic Data Masking (DDM)
Dynamic data masking (DDM) has emerged as a crucial security tool for organizations. It offers an effective solution by dynamically masking sensitive information in real time, ensuring that only authorized users can access the actual data while hiding it from unauthorized eyes.
What is Dynamic Data Masking (DDM)?
DDM is a data security technique that hides sensitive information dynamically within a database in real time. It allows organizations to control access to sensitive data without altering the original data itself. Sensitive data such as credit card numbers, social security numbers, or personal identification information can be masked using DDM. As a result, it mitigates the risk of data breaches and unauthorized access.
Static Data Masking (SDM) vs Dynamic Data Masking (DDM)
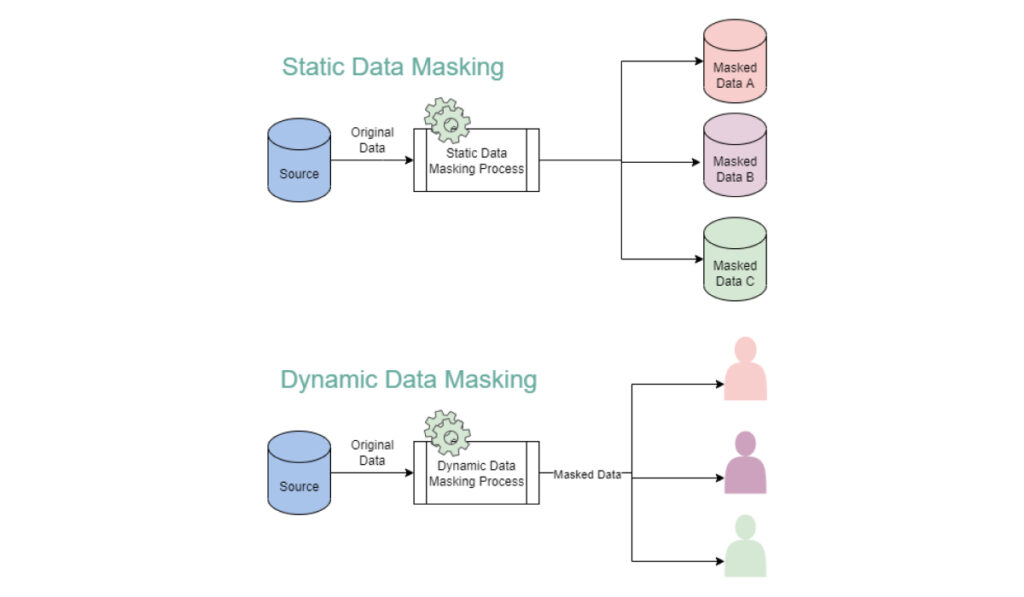
- SDM permanently alters sensitive data within a database to make it unreadable or meaningless to unauthorized users. DDM dynamically hides sensitive data within a database in real time. Unlike SDM, DDM does not permanently alter the original data; instead, it applies masking on the fly when users or applications access data.
- SDM typically involves creating a replica of the production database, hiding important data within this replica, and then using the masked data for development, testing, or analytics purposes. DDM employs masking rules and policies to selectively mask sensitive data elements based on user roles, permissions, or access privileges.
- SDM applies a one-time masking process to the entire dataset, resulting in a static set of masked data that remains unchanged until the next masking operation is performed. DDM operates in real-time and can selectively mask sensitive data based on user access permissions.
- SDM is commonly used in non-production environments, while DDM is used in production environments where real-time access to sensitive data is required for business operations.
Core Components of Dynamic Data Masking
1. Masking Rules
DDM uses masking rules to determine how sensitive data should be masked. These rules specify the types of masking techniques and the data portions that need to be masked. Here are some examples:
Credit Card Number Masking Rule
- Masking Technique: Substitution
- Rule: Replace all but the last four digits of credit card numbers with ’X’s.
- Example: Original: 1234 5678 9012 3456, Masked: XXXX XXXX XXXX 3456
Email Address Masking Rule
- Masking Technique: Redaction
- Rule: Hide the domain part of email addresses.
- Example: Original: example@email.com, Masked: example@xxxxxx.com
2. Masking Policies
Masking policies define the scope and application of masking rules within an organization’s database environment. These policies ensure consistency in data protection across various data sources and applications. Here is an example:
Financial Data Masking Policy
- Scope: Applies to all databases containing financial information.
- Rule: Mask all financial account numbers using encryption.
- Enforcement: Ensure compliance with PCI-DSS regulations.
3. Masking Functions
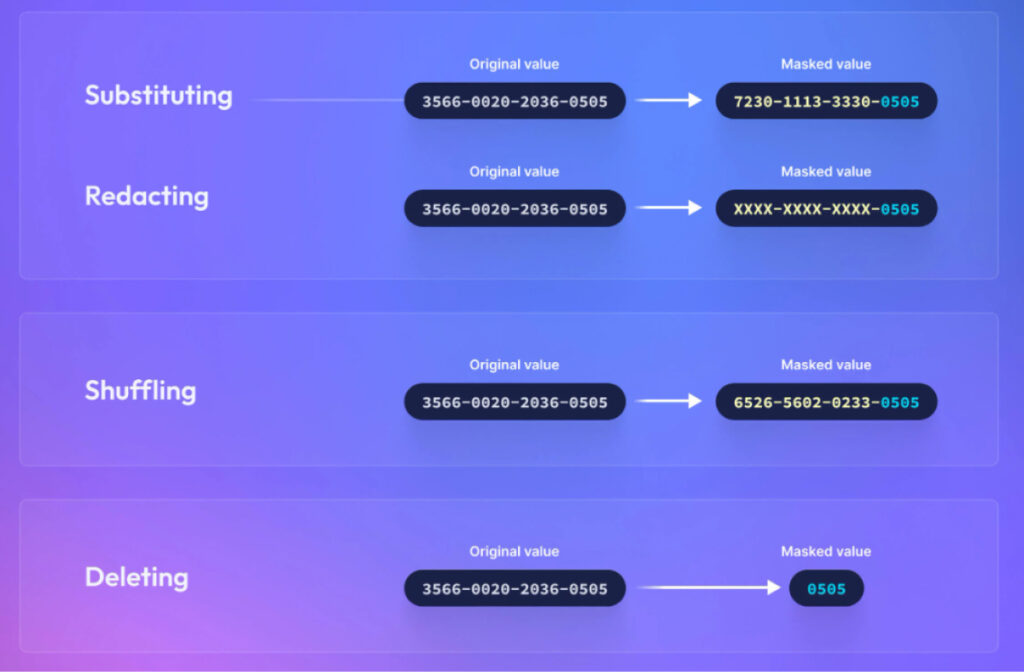
DDM uses various masking functions. These functions include techniques such as substitution, redaction, and shuffling.
Substitution
- Original: Social Security Number – 123-45-6789
- Masked: Social Security Number – XXX-XX-6789
Redaction
- Original: Medical Report – “Patient’s blood pressure is 120/80.”
- Masked: Medical Report – “Patient’s blood pressure is [REDACTED].”
Partial Masking
- Original Data: Phone Number – (555) 123-4567
- Masked Data: (555) XXX-XXXX
Conditional Masking
- Original Data: Customer Age – 25
- Masked Data (based on condition):
- Age > 18: 25 (unmasked)
- Age <= 18: XX (masked)
Data Peace Of Mind
PVML provides a secure foundation that allows you to push the boundaries.

Implementation of Dynamic Data Masking
Implementing DDM involves several steps:
1. Data Discovery and Classification
Organizations need to identify and classify sensitive data within their databases. This involves conducting thorough data discovery to identify sensitive information and categorize it based on its level of sensitivity.
2. Policy Creation and Management
Once sensitive data is identified, organizations can create masking policies that are suitable for the security requirements. These policies define which data elements should be masked and the masking techniques to be applied.
3. Integration with Existing Systems
DDM solutions must seamlessly integrate with existing database systems and applications. Compatibility with various database platforms and configurations ensures smooth implementation and minimal disruption to existing workflows.
Benefits and Challenges of Dynamic Data Masking
Benefits
- Protection of Sensitive Data: DDM helps organizations safeguard sensitive information from unauthorized access and data breaches.
- Minimal Impact on Performance: DDM solutions are designed to minimize performance overhead, ensuring that data masking operations do not significantly affect database performance.
- Compliance with Regulations: By masking sensitive data, organizations can demonstrate compliance with data privacy regulations such as GDPR, HIPAA, and PCI-DSS.

Challenges
- Complexity of Implementation: Implementing DDM requires careful planning and configuration, particularly in complex database environments.
- Maintenance and Updates: Ongoing maintenance and updates are necessary to ensure that masking policies remain effective and up-to-date with evolving security requirements.
- Performance Considerations: While DDM aims to minimize performance impact, organizations need to carefully monitor performance metrics to avoid any degradation in database performance.
Best Practices for Dynamic Data Masking
1. Regular Assessment of Masking Policies
Organizations should regularly review and update masking policies to adapt to new security requirements.
2. Role-Based Access Control (RBAC)
Organizations should implement role-based access controls to ensure that only authorized users have access to unmasked data. Assign privileges based on user roles, permissions, and responsibilities within the organization.
3. Continuous Monitoring and Adjustment
Organizations should continuously monitor data and usage. Based on unauthorized access attempts or anomalies, masking policies can be adjusted.
4. Employee Training and Awareness
Organizations should conduct employee training and awareness programs to ensure that personnel understand the importance of data security and adhere to masking policies and procedures.
5. Compliance with Regulatory Requirements
Organizations should ensure that DDM implementation complies with relevant data privacy regulations and industry standards, such as GDPR, HIPAA, or PCI-DSS. Regularly review and update masking policies to maintain compliance with changing regulatory requirements.
Wrapping Up
Dynamic data masking (DDM) offers an effective way to mask sensitive data in real time. By dynamically obscuring sensitive information within databases, DDM helps organizations mitigate the risk of data breaches and unauthorized access while ensuring compliance with regulatory requirements. There can be benefits as well as challenges in implementing DDM.
With careful implementation, monitoring, and adaptation, DDM can serve as a cornerstone of an organization’s data security strategy, providing peace of mind and protection in an ever-changing threat landscape.